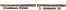 |
Misuse of Computer Essay Text
The association of police force chiefs england and wales fictitious group wanted a research report on the computer misuse. This group is unable to meet the challenges of e crime due to the continuous growth of crimes in the world of computers. This report includes the investigation about the computer misuse, a study on the computer misuse act. Gives a report on why the computer misuse act is unable to stop the continuous growth in the computer crimes. The report also includes the assessment on computer misuse act and the suggestions to the fictitious groups to prevent the crimes of computer misuse. Computer hacking: computer hacking is a technique of taking access over the unpermitted network or modem or other devices and the internet. The hackers usually try to grant admittance to the passwords and several different security sites in order to view the confidential information. Custom Admissions Essay UkExploitation of the data, unconstitutional relocation of the data or photocopying: the information available in the internet is copied through various sources like hard disks, dvds and pen drives. These types of informal moving of data are done simply with the use of the internet connections. Without having copy rights to access the personal information, research work of any company and novels, books written by the author's one cannot copy the information, but using some illegal techniques they gain access over this information. Distribution of the copied software's, movies and music: the software, movies and music is illegally copied without the copy right and they are distributed all over. They do not follow the laws and copy the material without taking permission from the copyright holders. Abusing people through chat rooms and emails: emails, chat rooms are used by some people who simply intend to disturb other individuals. The create email ids with improper identifications and spread news and rumors about famous personalities. They abuse people using chat rooms, they send spam mails to millions of people to market the goods and services that can be sometime legal, but many a times those which are illegal. Pornography: pornography is an illegal activity, and this type offensive stuff is exists on the internet and people store and keep this stuff in an electronic form. This kind of stuff has been declared illegal as they show all the illegal activities. Financial abuses and identities in this category, come the misuse of stolen credit cards and the fantastic numbers of the credit cards in order to purchase online products and service. A financial abuse also includes printing of unauthorized currencies using color printers. Virus is a software program written for causing damage and nuisance to the computers or files. In united kingdom, one of the significant and distinguished policies imposed by the government legislation to avoid the issue related with hacking of computers and virus programs that were being generated for destroying the files was the computer misuse act 1990. This act included three crimes, they are: the crime of unauthorized access the crime with hidden intents of disruptions. How to Write An Abstract for Your Dissertation UkThe crime of unauthorized modifications to provide security to the online users and to protect the confidential information from the people who misuse the computer is called as the computer misuse act. The faults under this act are the computer hacking, exploitation of the data, unconstitutional relocation of the data or photocopying, abusing people through chat rooms and emails pornography, financial abuses and identities and producing virus software's. Un permitted admittance to the computer system to make alterations in the computer programs, and other activities like changing the passwords of the systems and other type of setting that can cause inconvenience to the users, and preventing them to access their own systems is considered as a crime under the computer misuse act. Under the act of computer misuse, it is considered as crime to get admittance to the system or even if some try to take admittance without proper endorsement. Hence under this act if the hacker try to use the system and even though he his unsuccessful in his act, he will be found guilty. Using the email ids, chats and other similar services of other persons and causing obstinate harm to the system is a severe crime under this act. This act also considers the use of only a several parts of the system and if someone uses the other parts of the system then it will be a crime because they are not authorized to use them. Distribution of the copied software's, movies and music is not included under the computer misuse act but it is declared as a crime by several other legislations. If someone breaks the computer misuse act he has to either pay penalties or he can be imprisoned. According to peter somer, 29 november 2005 , daniel cutherbert was a software tester and in october 2005, he performed an illegal activity and got admittance to the website of tsunami charitable trust. He made a visit to the website and donated some �30 to the charity but due to the unsatisfying response from the website and the poorly designed graphics, he did not get a quick response from the site about his donation, and he became anxious to know what's actually going on. To check whether his donation got accepted or not he tried an abortive test of directory traversal and got some relief. How to Motivate Yourself to Do Homework When You Are TiredBut this test created a disruption in the disruption alarm and was found guilty as using that test was against the law. During his assessment the defense group support cutherbert that his intentions were not provide any harm to the website, or perform any illegal activity. Being a software tester he just used his skills to test the website and there is nothing wrong in using these tools. But the prosecution team opposed the defense team saying that he must be aware that using the traversal directory is against the law and willingly he did the crime. Another such case, young boy was left free from the court of wimbledon, though he accepted in the court that he has used a software program called as mail bomber in order to overflow the mail server of a well known insurance firm. Grading Rubric for Middle School Writing AssignmentHe produced some 5 million emails, but when he was suspected and arrested by the police, his defense team saying that every email sent to the email server was official otherwise the email would not get accepted, and there is no condition where all the 5 million emails can at once turn into unofficial emails. The above chart of computer crime in england and wales shows the computer crime reported in the year of 2006, 2007, 2008 in the different categories of computer crime. If we analyze each category one by one in year wise we get:
Sexual offences are increasing day by day as continuous increment is recorded in the year of 2007 as well as in 2008 also. Even though the government has imposed the computer misuse act, the laws of the act are not followed strictly by the people. But that is not the actual problem there the problem is with research on security that is existing today. The issue with security on computers is a critical issue and finding solutions for this issue is not at an easy job. This act does not permit the researchers from britain to participate in the community of universal security.
© Copyright 2013 - 2016 - www.writehomestudio.com.
All rights reserved. |
 |